Offices of Inspectors General (OIG): Auditing & Investigative Solutions
The internet is at the heart of the investigative process in the Offices of Inspectors General (OIG). We know you need unrestricted access to nefarious domains and common open source websites, programs, or tools for audits and investigations.
Fraud, waste, & abuse
Policy violations
Government oversight

Executive mismanagement
How Do You Fulfill OIG Requirements and Protect Your Organization?
Using a standalone laptop across multiple investigations can jeopardize mission safety and performance.
Without a comprehensive platform, you risk:
- Identity exposure
- Disjointed evidence management
- Counterattacks from investigative subjects
- Lack of operational oversight
The Ntrepid Advantage
In such a high-stakes environment, the OIG requires robust and streamlined managed attribution solutions with oversight capabilities.
To more efficiently achieve investigative missions like yours, we created Nfusion: a virtual desktop environment that empowers you to collect evidence, manage digital footprints, and oversee user activities—all with complete security.
What Nfusion includes:
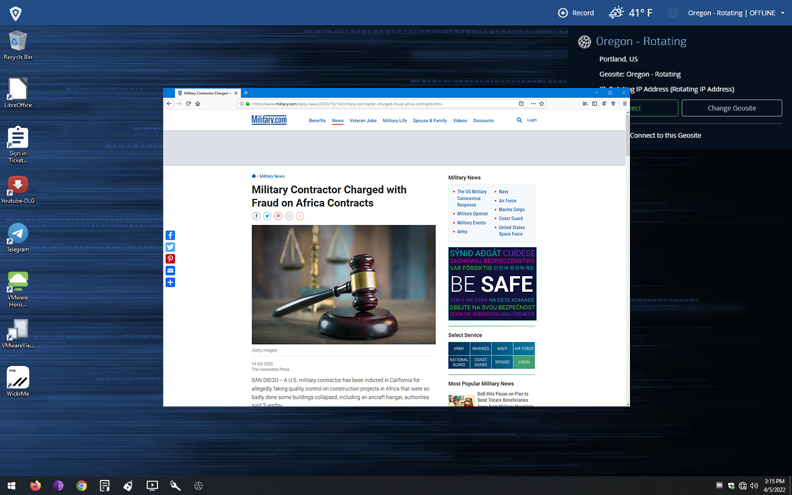
Managed Attribution Platform
- Wide array of egress points
- Total identity protection
- Obscured digital trails

24/7 Support
- Dedicated account manager and support
- OPSEC training
- Continuous R&D
Evidence Collection
- Integrated evidence collection tools
- Support for third-party desktop tools and web applications
- Screen captures of every browser page



