Lightbeam by Firefox Illuminates Managed Attribution Risks
You should know by now that, when you are online, you are always being watched—usually by many organizations at once. What you may not be aware of, however, is the extent of hidden, third-party sites that are viewing and monitoring your activity. Firefox offers Lightbeam, a free tool, for you to examine the scope of this issue.
Browsers are the primary tool used for online operations and investigations. In order to help websites customize their content for you, browsers are designed to share a tremendous amount of information with websites. That information is visible to far more than just the sites you are intentionally visiting.
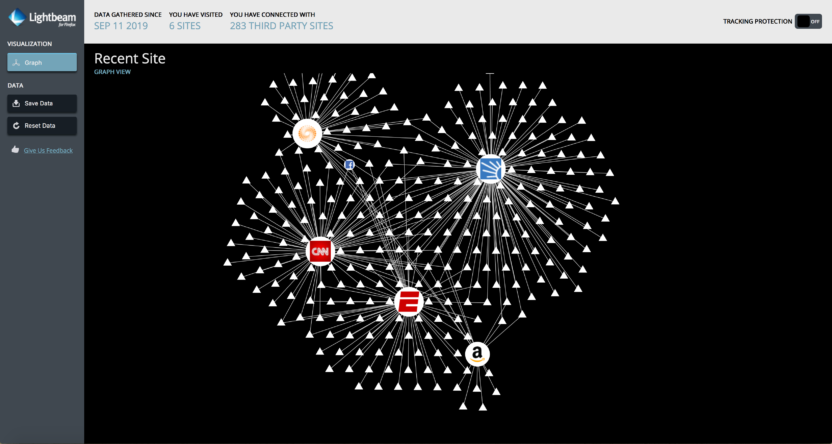
As you can see in the screenshot above, I visited 6 typical websites, but they are making connections with other sites. Just by visiting those 6 web pages, there are almost 300 other servers accessing my information. Most of them I have never heard of, and I know nothing about their management, intent, or trustworthiness.
Let’s consider the information available to any of these servers you see in this example. They can capture your IP address, network information, and browser and system fingerprint. The servers are also able to scan your system or set cookies and trackers on you to monitor your activity across the web.
If any of the servers are actual hostile entities or happen to be an organization that was hacked, the adversary could discover aliases, notice odd patterns of activity, and discover the exit nodes you use for managing attribution.
Even non-hostile services like social media platforms can leverage their visibility to discover and block alias or “fake” accounts. The “like” and “share” buttons that you see on almost every website are signaling back to the large social media platforms, allowing them to see your activity.
So how are you supposed to prevent this kind of exposure? Unfortunately, simply blocking all of these servers is not a good solution. Blocking leaves its own signature, clearly showing that you are trying to hide your identity. This makes you easily detectable by the observing services.
The only effective solution is to perfect your operational security (OPSEC) and discreet activity. Because the threat actors can see activity across a wide range of sites, identities need to be kept well separated from one another. Multiple aliases using the same IP address or browser will be easily detected. Even if two identities never visit the same website, these services will still be able to connect with them. There are two approaches to ensure you are not exposed. One is to use a single IP per alias. The other is to use shared IPs (like cellphone IPs or shared WiFi), but they need to be shared by a lot of people to look realistic.
You also need to ensure that the fingerprints of the alias environment are varied but all well within typical configurations. The device used for browsing should not be locked down or configured in a way that is unusual to the servers. It is important to use operating systems and browsers that are typical to the users of the websites you visit. A secure, anonymous Linux would stand out among visitors to a site like Pinterest.
Ubiquitous monitoring of online environments is a reality we can’t deny or avoid. The only way to ensure continued success in managed attribution operations for OSINT or investigations is to adapt your practices to address this ever-increasing threat.
You can watch the full video here.









