How to Prevent Ransomware
One morning you sit down with your cup of coffee and turn on your computer expecting to check email and possibly browse the latest social media news.
Instead you are greeted with a message similar to this:
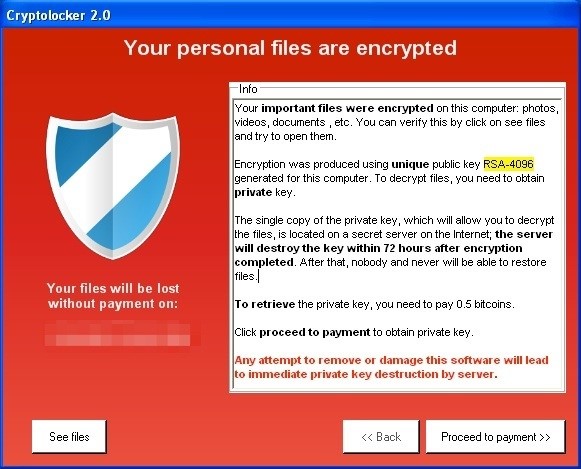
You have become a victim of “ransomware,” or more generally “crimeware.” Understandably, a barrage of questions will run through your mind:
- What do you do now?
- What information has been exposed?
- Is your personal information now available on one of the numerous criminal forums?
What are crimeware and ransomware?
Crimeware is malicious software designed to make money from hacking your computer. Crimeware steals passwords, captures credit card numbers, and even accesses bank accounts. However, the type of crimeware called ransomware is particularly nasty because it encrypts all of your data — often including your backups — and demands payment to provide the decryption key.
It seems that every day the media and security professionals are reporting yet another zero-day vulnerability being actively exploited by one of the prolific crimeware packages. Software companies attempt to release updated patches to address the security holes but not before thousands of personal and corporate assets are compromised. This article provides an overview of a process that will help protect your computer from criminals working to gain access to your personal information.
The first step for criminals is to gain access to a user’s computer. This access can be gained by many different ways but the goal of access remains the same. Once access is gained then the criminals begin to gather information or conduct other activities.
Any crimeware will attempt to dig in once it manages to penetrate your computer. It will try to make sure that it’s hard to detect, and that it runs automatically when the computer starts. Typical crimeware tries to stay active as long as possible to capture all of your valuable personal information from your keyboard, emails, or files. Ransomware is even trickier and insidious. While it slowly goes about the process of encrypting all the data on your hard drive, it modifies some system drivers so the files continue to appear normal. You can continue to open, read, and edit these files even though they are actually encrypted on the disk.
Ransomware does this for two reasons. First, it wants to do the encryption slowly so the impact on your computer’s performance is not noticeable. Second, and more evilly, it wants to wait until all your backups of your files also contain the encrypted version of the files. It might take months to ensure that no clean backups are still around. At that point, the ransomware deletes the key from your computer, making all your files inaccessible, and pops up the alert at the beginning of this article.
So, what can you do to protect yourself?
Anything that is of value must be protected by multiple levels of security — a strategy known as defense in depth. If any one of the levels fails, the others are in place to prevent further intrusion or compromise. It’s like a moat surrounding a castle with a tower in the middle. An attacker would need to swim the moat, climb the wall and breach the tower to reach the jewels within. Here are some of the layers of security you can put in place to protect yourself. While none are a silver bullet, together they provide substantially improved protection against online criminals.
1. Use encryption when you email or store any sensitive information.
Malware can access anything on your computer. If it is stored encrypted it is more difficult for the malware to steal.
2. Create multiple versions of your backups and keep them around for a long time.
A saying in the security community is that “one is none” when it comes to backups. Best practices are to have at least three independent backups with at least one of those being off site. Keep backups for as long as possible to maximize your ability to recover files after a ransomware attack.
3. Don’t reuse passwords on different websites.
An attacker may only be able to capture a fraction of your usernames and passwords, but if they are all the same they can use them to break into all of your other accounts. This also provides protection against breaches of any of the sites you visit then compromising your security on other websites. A password manager makes this easy, and also helps you generate strong passwords. If you can remember a password it is probably too weak.
4. Freeze your credit reports.
Keep a freeze on your credit reports at all times, not just when you have become a victim of identity theft. You have little to no liability for purchases made with a stolen credit card, but new loans and cards taken out in your name could damage your credit rating for years, and take endless hours to resolve. A credit freeze will prevent anyone from opening new credit in your name, even if the hacker manages to steal your information.
5. Enable two factor authentication on accounts.
When available, this provides powerful protection against the attacker using stolen usernames and passwords. Two factor authentication requires a token, your cell phone, or some other unique thing you possess in order to access your account. Just username/password alone, is not enough.
6. Establish a clean baseline environment.
Finally, you can ensure that malware is eliminated by starting with an immutable working environment which always starts in a known good and clean condition. Running from a bootable CD or doing all your work in a virtual machine that you roll back at the end of each day can ensure any undetected malware is destroyed within a short time. This can be a lot of work to do on your own but effective tools exist, like virtual secure browsers, to automate this process.
Even if you don’t implement all of these suggestions, just putting a few into practice can make you much less likely to suffer the pain of crimeware and ransomware.









