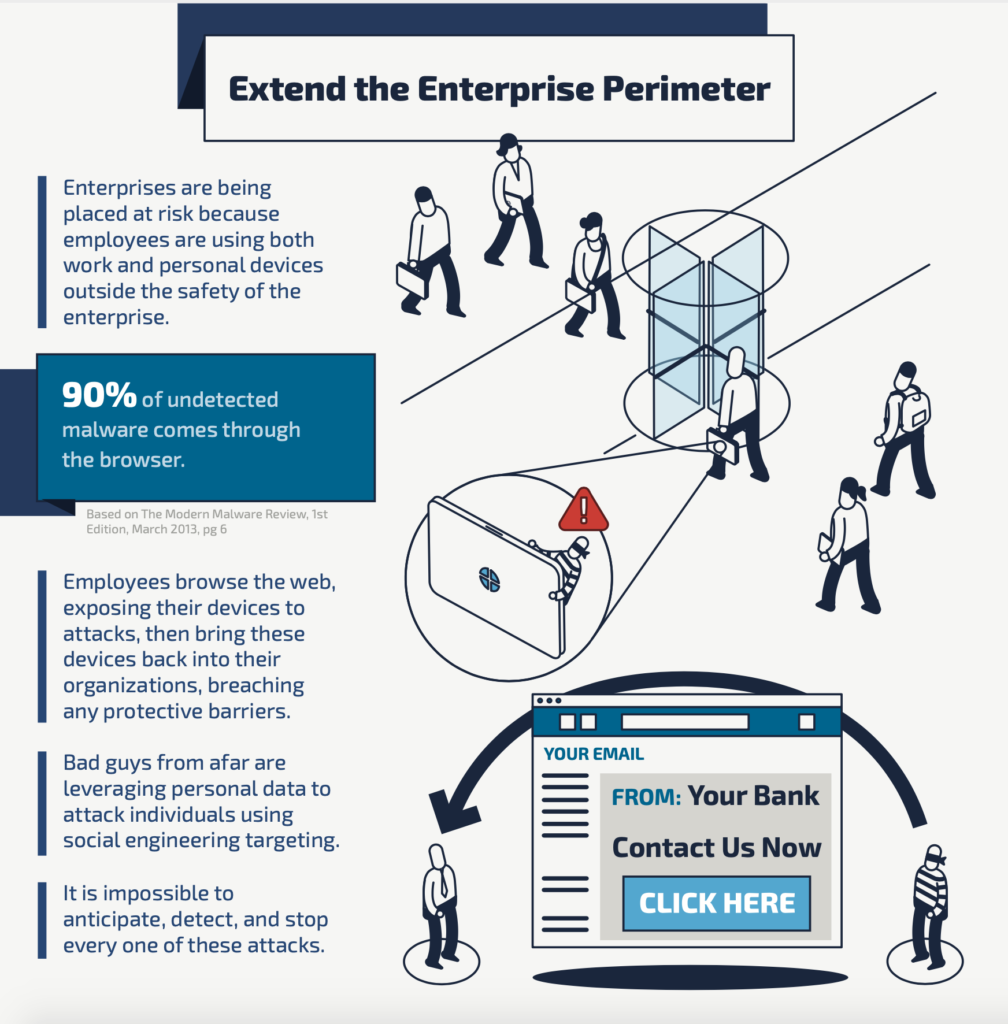
A Visual Approach to Extending the Enterprise Perimeter
Today’s mobile workforce has effectively eliminated the traditional enterprise perimeter that we once relied upon. This transient workforce has made it risky to assume that employees are protected from web-based attacks even if they are within the limits of their organization’s physical campus or digital network. Based on our 2016 report with ESG, we know that internet use is a critical part of business operations, but the web browser remains an extremely vulnerable attack vector. To demonstrate this, we have created an infographic on the importance of extending the enterprise perimeter.
Organizations must take a new approach to securing the enterprise by rethinking the nature of perimeters and by extending their protections to the individual.
Studies have found that roughly 90% of undetected malware comes through the browser, which means that there is a very good chance employees will expose their devices to attacks when browsing the web. Even if an organization has top notch security, what happens when employees use devices at home or in a coffee shop? And worse, what happens when they bring these potentially infected devices back to the workplace?
Attackers are leveraging personal data to attack individuals using targeted social engineering, then leveraging those footholds to impact the company they work for. While it is impossible to anticipate, detect, and stop every one of these attacks, technology has been created to isolate the browser and potential attacks from the local network. This way, when employees inevitably open a malicious link or visit a bad website, attacks are contained and ultimately destroyed.
Isolated, virtualized browsers like Passages help reduce the time and effort spent flagging attacks on a company’s network. By quarantining web traffic within a dedicated environment, Passages aids in protecting organizations from any form of browser-related exploits. As the internet continues to become more complex, browser security has not kept pace. It has become clear that the use of traditional browsers will leave organizations vulnerable to a plethora of potential attacks.
Only by extending the enterprise perimeter to include all internet activity of employees, can companies hope to fully protect the organization. At Ntrepid, we like to say that if you protect the individual, you protect the enterprise. To view our full infographic, Extend the Enterprise Perimeter, and learn more about browser isolation, download it below.