What Threat Actors See: Managed Attribution Threat Modeling
My previous blog on threat modeling for managed attribution presented a basic framework for analyzing the MA solutions you might use to protect your online operations. In this post, I further analyze the kinds of information that could be visible to the various categories of threat actors.
Accordingly, if you have not already visited Part 1, 2, or 3, of my series on threat modeling for managed attribution, you may want to read those pieces first in order to familiarize yourself with the threat modeling framework.
Watch the full video here.
In the context of managed attribution, threat actors include anyone who can see any aspect of your online activity, potentially revealing aliases or exposing your real identity. Many different entities qualify as threat actors, and each has the potential to obtain your sensitive information. The kinds of information at risk of discovery depend on the type of risk you face.
Let’s explore a few examples below.
Threat actors who are “On the Wire” can view your data packets in transit. Information at risk of exposure to these entities depends on their location in the data path. If the entity can see traffic between two nodes in a data chain, they would only have the ability to perceive the encrypted VPN packets. The node’s IP addresses, as well as the quantity and patterns in the traffic, would be visible, but the original source, destination, or content of the communications would not.
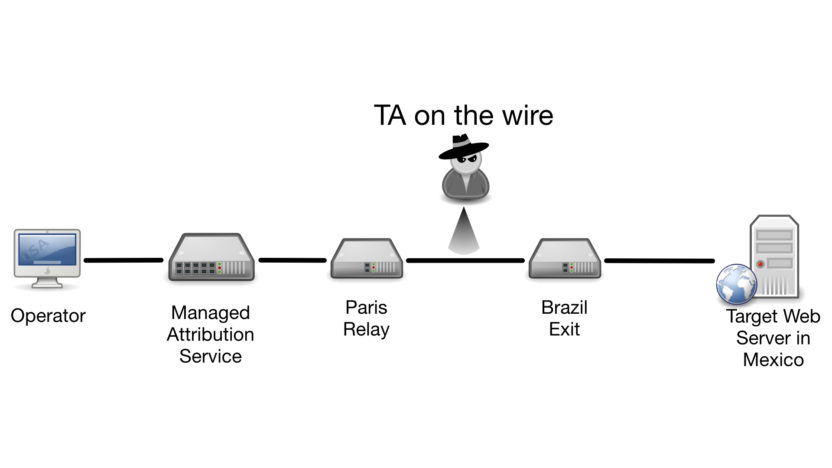
However, if the threat actor has access to the communications between your exit node and the destination, they could view greater amounts of identifying information.
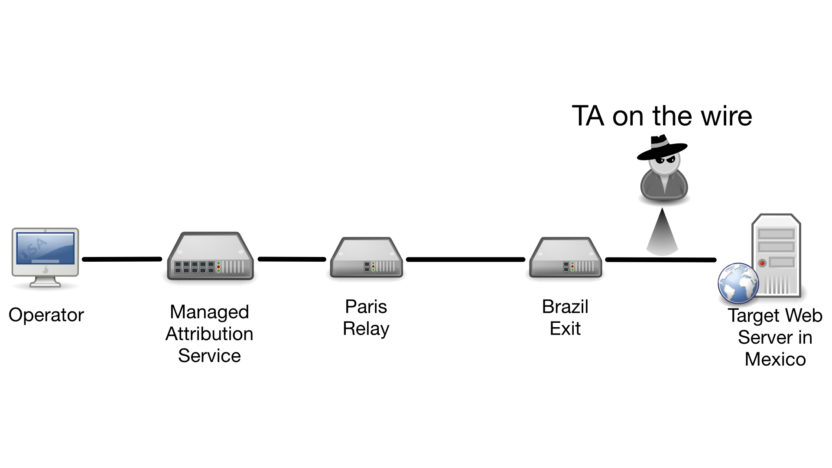
Threat actors sitting off of the end point would know the destination of the connection, and be able to read any unencrypted communications, see the services and protocols being used, and discover the IP address and configuration of the exit node.
When you’re undertaking a cyber operation, every service you use is a threat actor. Service providers with a high level of access to your information can inspect content, search behaviors, browser fingerprints, and other details.
Even the hosting companies that provide your relay nodes qualify as threat actors. In addition to accessing all the traffic flowing in and out of the server, hosting companies often have the ability to access the server and change the filesystem. These entities could also analyze the software that has been installed, any special web tools, and even cryptography keys.
As I discussed in my last post, threat actors also have profile characteristics that inform the actions they are likely to take with the information that is available to them. These characteristics include interest level, skill level, and their relationship to you. The impact of a threat actor varies according to how they align with each of these dimensions.
When developing your threat model, consider every entity that could possibly be a threat actor. Catalogue the information available to each of them, and analyze their likely profile based on the dimensions from my threat model framework. Keep in mind that the profile characteristics may differ greatly if their services have been compromised by unfriendly entities.
Every type of threat actor has access to different kinds of information about your activities. Thus, if you thoroughly consider the actors in your own threat model, you can optimize risk responses to protect your operations.









